Celebrating CyberStart - where cyber security training was brought to life through real-world hacking challenges and puzzles
After 9 wonderful years of bringing gamified cyber education to young people across the globe, CyberStart is now closed.
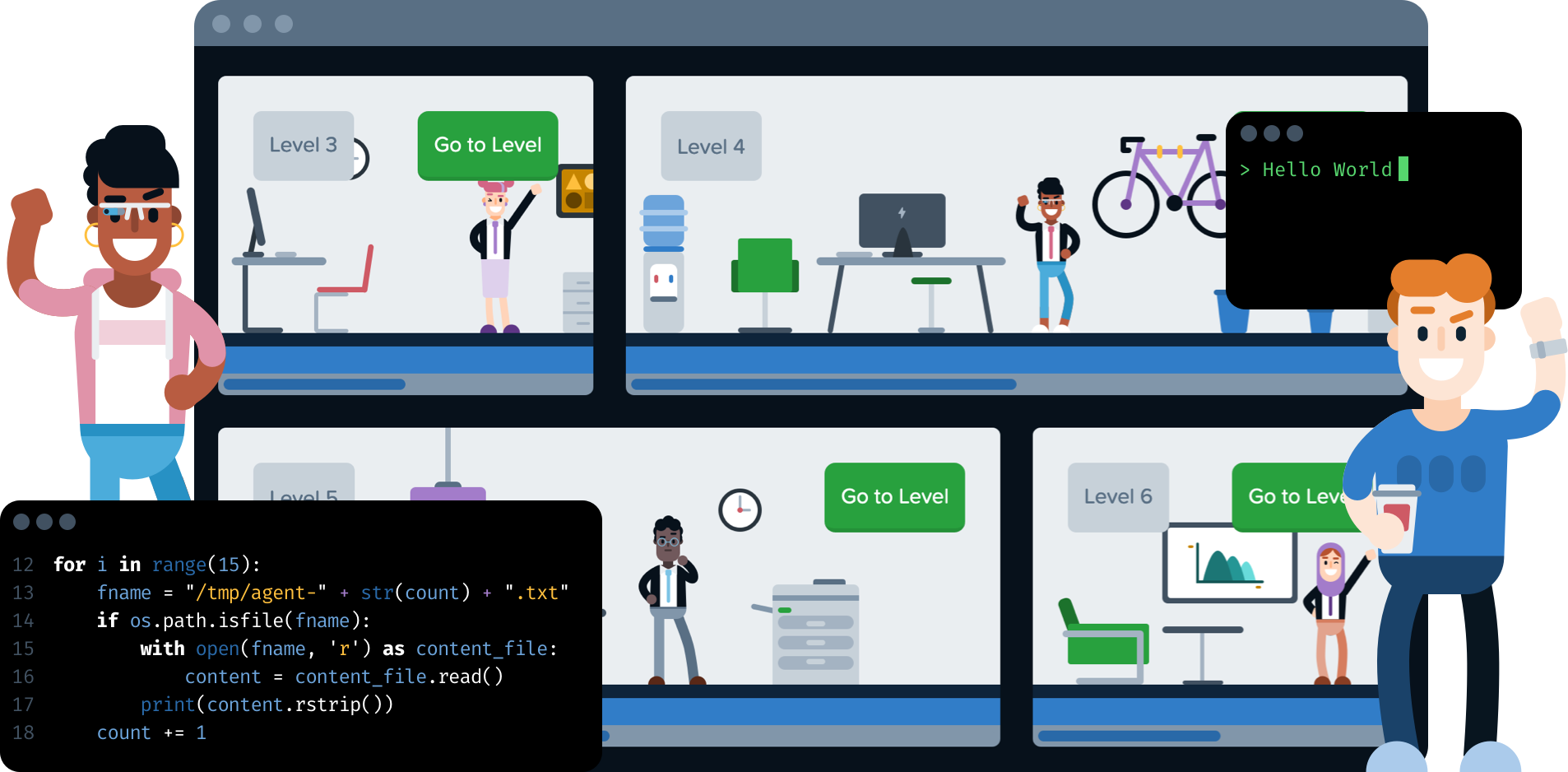
The immersive cyber security training game that changed the global security landscape for good
Join us in celebrating the legacy of this groundbreaking product, the team that built it, and the many dedicated and talented players who will soon form a significant part of the world's cyber workforce.
The game
Cracking passwords, finding hidden messages and experiencing life as an ethical hacker in an immersive learning experience - players solved mysterious puzzles, unlocked levels and sharpened their offensive and defensive security skills in the role of a cyber crime investigator.
The team
Meet the team who built CyberStart - a unique blend of people with diverse abilities, all working towards the same goal of providing an innovative educational platform to inspire the next generation of cyber security professionals.
The programmes
The cornerstone of a diverse array of education programmes, from high school initiatives nurturing budding talents to university partnerships fostering advanced skill development, CyberStart has been instrumental in empowering learners of all backgrounds.

The legacy
The pioneering game platform has left an indelible mark on the cyber security landscape. Through its innovative approach of gamifying cybersecurity education, CyberStart has empowered countless individuals worldwide to develop critical skills and pursue careers in this vital field.